Extending the AD Schema on Samba4 - Part 2
Importing LDIF files into Samba4 and Active Directory
This is part 2 of the Extending AD Schema on Samba4 series. The examples below are tested using the Samba4 LAB I created. If you want more information on how that works then please read http://david-latham.blogspot.co.nz/2012/12/samba4-ga-release-virtualbox-lab.htmlFor part one, please read http://david-latham.blogspot.co.nz/2012/12/extending-ad-schema-on-samba4.html
Unfortunately the format of an ldif file for creating new attributes and classes in the Schema Configuration are differ between Samba4 and Microsoft.
The tools are slightly different too. So this article will attempt to make it all clear.
Find all the latest versions of code on this post at https://github.com/linuxplayground/yubikey-ldap/tree/master/microsoft-schema
Samba4 - ldbadd & ldbmodify
As far as I can tell the only way to create a new class with a custom attribute in Samba4 (on the Linux command line) is first add the attribute with ldbadd and then add the class with a seperate ldbadd followed by an ldbmodify command to update the User schema to include the new auxiliary class.
I wrote a README.md file for when this eventually ends up on GIT. Rather than retype it all, I shall just copy it as is:
YubiKey LDIF Implimentation Into Samba4 Active Directory
=======================================================
This is an implimentation of the Openldap implimentation by Michal Ludvig <http://logix.cz/michal/devel/yubikey-ldap/> applied to Samba4 Active Directory.
CAUTION
-------
This process will permanently modify your schema. If it breaks you will not be able to recover unless from a backup. Please backup your schema files before starting. On a default install they can be found at /usr/local/samba/private/sam.ldb and all the files in /usr/local/samba/private/sam.ldb.d/
yubikeyid.ldif
--------------
dn: CN=yubiKeyId,CN=Schema,CN=Configuration,dc=samba4,dc=internal
changetype: add
objectClass: top
objectClass: attributeSchema
attributeID: 1.3.6.1.4.1.40789.2012.11.1.2.1.1
cn: yubiKeyId
name: yubiKeyId
lDAPDisplayName: yubiKeyId
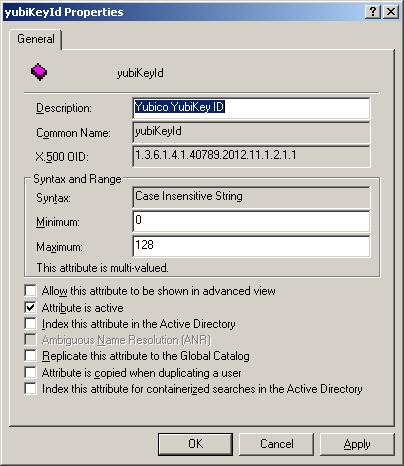
description: Yubico YubiKey ID
attributeSyntax: 2.5.5.5
oMSyntax: 22
isSingleValued: FALSE
Add the yubiKeyId attribute into the Schema Configuration first with:
ldbadd -H /usr/local/samba/private/sam.ldb \
yubikeyid.lidf \
--option="dsdb:schema update allowed"=true
yubikeyuser.ldif
----------------
dn: CN=yubiKeyUser,CN=Schema,CN=Configuration,dc=samba4,dc=internal
changetype: add
objectClass: top
objectClass: classSchema
governsID: 1.3.6.1.4.1.40789.2012.11.1.2.2.1
cn: yubiKeyUser
name: yubiKeyUser
lDAPDisplayName: yubiKeyUser
description: Yubico YubiKey User
subClassOf: top
objectClassCategory: 3
mayContain: yubiKeyId
Next add the yubiKeyUser class into the Schema Configuration with:
ldbadd -H /usr/local/samba/private/sam.ldb \
yubikeyuser.lidf \
--option="dsdb:schema update allowed"=true
updateUserClass.ldif
--------------------
dn: CN=User,CN=Schema,CN=Configuration,DC=samba4,DC=internal
changetype: modify
add: auxiliaryClass
auxiliaryClass: yubiKeyUser
Apply the User class update with:
ldbmodify -H /usr/local/samba/private/sam.ldb \
updateUserClass.ldif \
--option="dsdb:schema update allowed"=true
Add YubiKeys to Users
---------------------
An example ldif:
dn: CN=David Latham,CN=Users,DC=samba4,DC=internal
changetype: modify
add: objectClass
objectClass: yubiKeyUser
-
add: yubiKeyId
yubiKeyId: abcdefgh1234
yubiKeyId: xyzxyz123456
Apply it with:
ldapmodify -h samba -f addKeyToUser.ldif
Test it with:
ldapsearch -h samba -b "CN=David Latham,CN=Users,DC=samba4,DC=internal" yubiKeyId
SASL/GSSAPI authentication started
SASL username: administrator@SAMBA4.INTERNAL
SASL SSF: 56
SASL data security layer installed.
# extended LDIF
#
# LDAPv3
# base
# filter: (objectclass=*)
# requesting: yubiKeyId
#
# David Latham, Users, samba4.internal
dn: CN=David Latham,CN=Users,DC=samba4,DC=internal
yubiKeyId: abcdefgh1234
yubiKeyId: xyzxyz123456
# search result
search: 5
result: 0 Success
# numResponses: 2
# numEntries: 1
Acknowledgments
===============
Michal Ludvig for defining the schema.
Microsoft Documentation for information on attributeSyntax, oMSyntax and objecClassCategory
Active Directory & the LDIFDE tool
Use the following ldif file and the ldifde tool as described in the README.md below:
YubiKey Implimentation in Microsft Active Directory
===================================================
This is an implimentation of the Openldap implimentation by Michal Ludvig <http://logix.cz/michal/devel/yubikey-ldap/> applied to Microsft Active Directory.
Notes
-----
In order to manage the Schema from a Windows client, please add the following line to your smb.conf under the [globals] section and restart samba4:
dsdb:schema update allowed = true
You can use tools like ADSI Edit to manage the keys for users.
There are also tutorials on the internet explaining how to crate a dialogue box / context menu tool for updating custom attributes in the Active Directory Server Admin tool. (dsa.msc)
For a complete tutorial on all of this look at:
<http://www.informit.com/articles/article.aspx?p=169630&seqNum=1>
Implimentation
--------------
Log into a Windows Server 2003 as a domain administrator and start a
command prompt.
Then execute:
ldifde -i -f path\to\yubikey-ads.ldif -j .
You should see something like:
6 entries modified successfully
The command has completed successfully
To test if this is all working you could add some kuys using the ADSI Edit
snap-in.
* Browse to your Domain -> CN=Users
* Right mouse click the username you want to edit
* Select Properties
* Scroll down to and select YubiKeyId
* Click Edit
* Add values until you are done
* Click OK until you are finished.
The LDIF File
## YubiKey LDAP schema for Microsoft Active Directory Server
#
# Install with ldifde -i -f path\to\yubikey-ads.ldif -j .
# on a Windows Command prompt
#
#
# Author: Michal Ludvig
# Consider a small PayPal donation:
# http://logix.cz/michal/devel/yubikey-ldap/
#
# Converted to Microsoft Active Directory Server format by
# David Latham
#
dn: CN=yubiKeyId,CN=Schema,CN=Configuration,DC=samba4,DC=internal
changetype: add
objectClass: top
objectClass: attributeSchema
cn: yubiKeyId
description: Yubico YubiKey ID
attributeID: 1.3.6.1.4.1.40789.2012.11.1.2.1.1
attributeSyntax: 2.5.5.5
isSingleValued: FALSE
oMSyntax: 22
lDAPDisplayName: yubiKeyId
name: yubiKeyId
dn:
changetype: modify
add: schemaUpdateNow
schemaUpdateNow: 1
-
dn: CN=yubiKeyUser,CN=Schema,CN=Configuration,DC=samba4,DC=internal
changetype: add
objectClass: top
objectClass: classSchema
cn: yubiKeyUser
description: Yubico YubiKey User
subClassOf: top
governsID: 1.3.6.1.4.1.40789.2012.11.1.2.2.1
mayContain: yubiKeyId
rDNAttID: cn
objectClassCategory: 3
lDAPDisplayName: yubiKeyUser
name: yubiKeyUser
dn:
changetype: modify
add: schemaUpdateNow
schemaUpdateNow: 1
-
dn: CN=User,CN=Schema,CN=Configuration,DC=samba4,DC=internal
changetype: modify
add: auxiliaryClass
auxiliaryClass: yubiKeyUser
-
dn:
changetype: modify
add: schemaUpdateNow
schemaUpdateNow: 1
-
Comments