Extending the AD Schema on Samba4 - Part 2
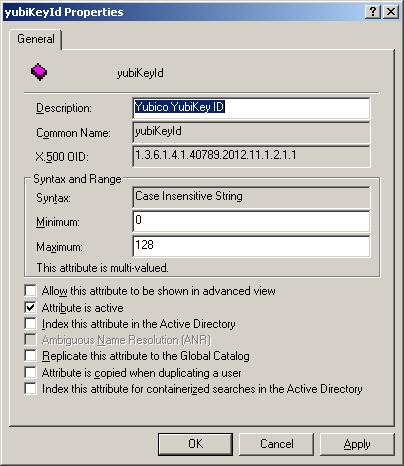
Importing LDIF files into Samba4 and Active Directory This is part 2 of the Extending AD Schema on Samba4 series. The examples below are tested using the Samba4 LAB I created. If you want more information on how that works then please read http://david-latham.blogspot.co.nz/2012/12/samba4-ga-release-virtualbox-lab.html For part one, please read http://david-latham.blogspot.co.nz/2012/12/extending-ad-schema-on-samba4.html Unfortunately the format of an ldif file for creating new attributes and classes in the Schema Configuration are differ between Samba4 and Microsoft. The tools are slightly different too. So this article will attempt to make it all clear. Find all the latest versions of code on this post at https://github.com/linuxplayground/yubikey-ldap/tree/master/microsoft-schema Samba4 - ldbadd & ldbmodify As far as I can tell the only way to create a new class with a custom attribute in Samba4 (on the Linux command line) is first add ...